For the third straight year, Drs. Daniel Solove and Paul Schwartz held their Privacy and Security Forum at George Washington University Law School. For the third straight year I attended and presented. This year’s forum was the biggest ever and like the previous years, was packed with different sessions on issues ranging from GDPR to Industrial Control System security.
Dave Tyson of CISO Insights and I spoke about Governance. We focused on how the Security function fits within the business by means of Governance activities.
Defining governance is tricky so we started with the justification for it. Why governance?
Governance enables organizations to:
- Ensure senior management direction is applied to security risks
- Make risk/investment trade-off’s
- Meet their fiduciary responsibility for oversight
- Create an ongoing communication process to continuously improve
Moreover, organizations with top tier risk management programs are also the most profitable businesses.
Having gone into each of these points for a bit, we still had not defined governance and had not yet dropped the bombshell that really effective governance means seemingly taking the CISO down a notch.
So, we presented some framework level definitions as a baseline:
- ISO 27001: 2013
- 3 Management review: Top management shall review the organization’s information security management system at planned intervals to ensure its continuing suitability, adequacy and effectiveness.
- NIST Cybersecurity Framework
- Governance (ID.GV): The policies, procedures, and processes to manage and monitor the organization’s regulatory, legal, risk, environmental, and operational requirements are understood and inform the management of cybersecurity risk.
Governance is about management and it’s about risk and it’s about risk management—all three (and they can be seen as discreet). So, not surprisingly, when you dig deeper you start thinking of governance not just as a top down activity but as something that can serve both strategic and tactical objectives (in ISO terms: “suitability, adequacy and effectiveness”). Grabbing the Risk Management graphic out of the NIST Cybersecurity Framework, we annotated it to indicate the different spots where governance should occur.
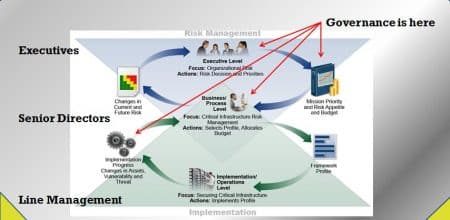
A traditional view of governance has it occurring only at the Executive level. But Senior Directors who are business process leaders also can have a role in governing the security function, even if their authority leaves them more as advisors than approvers. The business process level is where effectiveness is measured and therefore managed/governed at the tactical level. This assumes that management within the enterprise is collaborative.
Regardless of level, governance succeeds when it is a crucial input to the management of the Security Program. In order to accomplish this, governance bodies need more than just metrics and discussion topics. They need to be allowed to have input into the agenda and priorities of the Security Program itself.
Too often, the Governance function is reduced to approving budgets for Security. Too often, the CISO alone sets the agenda for the Governance Committee meetings. And way too often, while resources and project plans are presented to Governance Committees, the operational side of the Security Program is left un-discussed.
And so, Dave and I argued, you have to, in a sense, demote the CISO. Or more accurately, charge them with involving key stakeholders in shaping the Security Program at an organization. For the “command and control” type of CISO, this collaborative approach may be difficult to adopt.
Certainly, there is a technical side of the CISO’s role that is best left outside the Governance Committee meetings as well (regardless of what level the members are at). For example, I once heard a CISO explain how he had been telling a CFO why different 802.11 wireless protocols were better than others. He did not last long at that organization.
But assuming the right level of discussion, the CISO’s role is to engage the organization in all aspects of security. And for that to happen, they need to allow those involved in governance actually govern.


